What are you interested in?
Institutional Investors and LPs
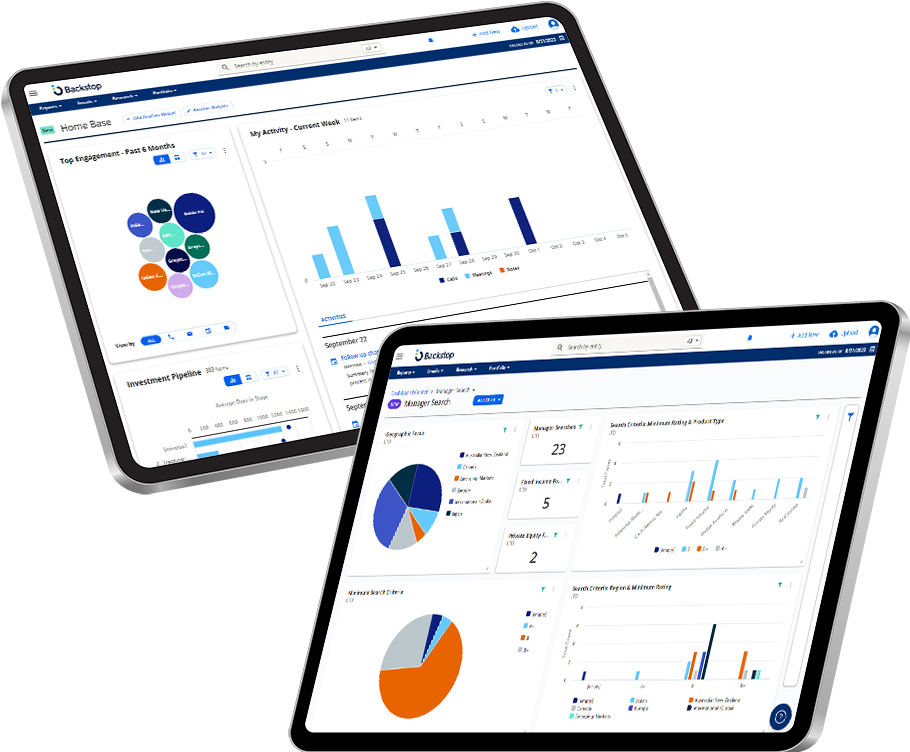
Future-proof your investment process with a single, dynamic source of truth encompassing both quantitative and qualitative data. Backstop’s, multi-asset-class research and portfolio management platform eliminates silos, enabling your teams to make well-informed investment decisions effortlessly.
Learn morePrivate Fund Managers (GPs)
Discover a dynamic, adaptable platform that will truly set your firm apart. Backstop empowers you with the ultimate single source of truth – revolutionize how you raise and retain capital, supercharge business development, and foster meaningful connections with allocators, consultants, and other industry participants in your universe. Unlock your firm’s full potential today.
Learn moreConsultants, Advisors & OCIOs
Backstop is your trusted ally in optimizing the investment and client life cycle. Our solutions create a single source of truth for multi-asset research and portfolio management, driving prospect and client satisfaction, fostering loyalty and ensuring long-term retention. Stay ahead of the competition with Backstop’s cutting-edge solutions.
Learn moreExplore our comprehensive services
Our configurable suite of intelligent, interlocking technologies.
Explore Backstop Data Services
The right data, right where you need it.
Streamline due diligence, document retrieval and management with automated processes
IntellX automatically retrieves crucial documents from fund source emails and portals, seamlessly connecting them to corresponding funds and investments. Unlock efficiency and empower your team with instant access to valuable resources.
Automatically feed custodial data into Backstop
Save your team countless hours with accurate, and automatic posting of custodian data. It’s never been easier to safeguard your assets, reconcile returns and harness real-time insights to drive your decisions.
Put vital fund admin data at your team’s fingertips
Set the stage for transparent, truly first-class investor service with performance reporting, capital activity, and investor balance information automatically loaded into Backstop.
Digitize and streamline form-based due diligence
Our new integration enriches your form-gathering process for faster, more efficient portfolio monitoring, research management and investment due diligence.
Power your data strategy with our APIs for an efficient and streamlined approach to data management.
Empower your in-house developers to integrate Backstop securely with a range of mission-critical systems, third-party applications, and external reporting engines, using robust, specially licensed REST APIs.
Gain a wealth of comprehensive insights into hedge funds and industry trends
Use our market leading platform to access instant, valuable proprietary research on portfolio management and performance assessment for hedge funds, CTAs, UCITS funds, and alternative investment vehicles.
Resources
Immerse yourself in our resource library and witness the transformative power of Backstop on your investor and investment lifecycle. Dive into our blogs, thought leadership, solution briefs, datasheets, and customer success stories.
View allWhat Our Clients Say About Us

Backstop is very customizable…the client/marketing team has been able to build out our instance and do a lot with it. The support team is very responsive. The report builder has been extremely useful for our client team, and the ETK function even more so.
Katie Carroll

I work in Backstop 8 hours a day, 5 days a week. It is our document database and main data depository. It provides us with the tools we use on a daily basis to both analyze and house our data and all the documents that we receive. Besides ease of use, ease of reporting, and ease of viewing, the Backstop Support people are top of class.”
Kathy McLean

Backstop has been a great solution for our firm and working with Backstop has been a great experience since the very beginning.
Jono Swanson

Backstop is the most flexible and intuitive
CRM system I’ve used.
Maria Szabo

By using Backstop, our managers can easily access financial information and analysis anytime when making investment decisions.
Camilla Burke

It is an excellent product, allowing us to effectively “mirror” our Trustee record keeping; which provides us the ability to reconcile and identify any potential errors and strengthens our level of assurance
Rosele Watro

Backstop allows us to maintain the organization’s memory. Turnover is an unavoidable truth in any institution. As people go, they take with them crucial knowledge. Backstop is how we can mitigate this…the system helps to keep track of all the conversations we have and all the people we have them with.
Mark Montoya

I have used several other systems in my days and this one is by far the best, most tailored to the asset management industry and with the most user-friendly features.
Julie Platt Smith

Breadth of functionality. Quality of customer service. Strong focus on innovation, product improvement, and customer needs.”
Rip Mecherle

Great relational database for information tracking, contact management, client management, distribution, and accounting.
Chris Arends

Backstop is a key client engagement tool within our advisory business. Their customized software configurability and flexibility, along with client service, have made Backstop a key partner for our firm,
David Gold

Backstop is very customizable…the client/marketing team has been able to build out our instance and do a lot with it. The support team is very responsive. The report builder has been extremely useful for our client team, and the ET function even more so.”
Katie Carroll

It fills a huge void we had in tracking managers, contacts and performance. User friendly, responsive support.